Sigstore Cosign Signature Verifiers
Configuring Sigstore/Cosign Verifiers for Requiring Image Signing
NeuVector enables a user to perform signature verification logic by integrating image signatures generated by Sigstore's cosign tool.
The following is an example of an admission control configuration that requires a deployment's image be signed by an appropriate key or identity.
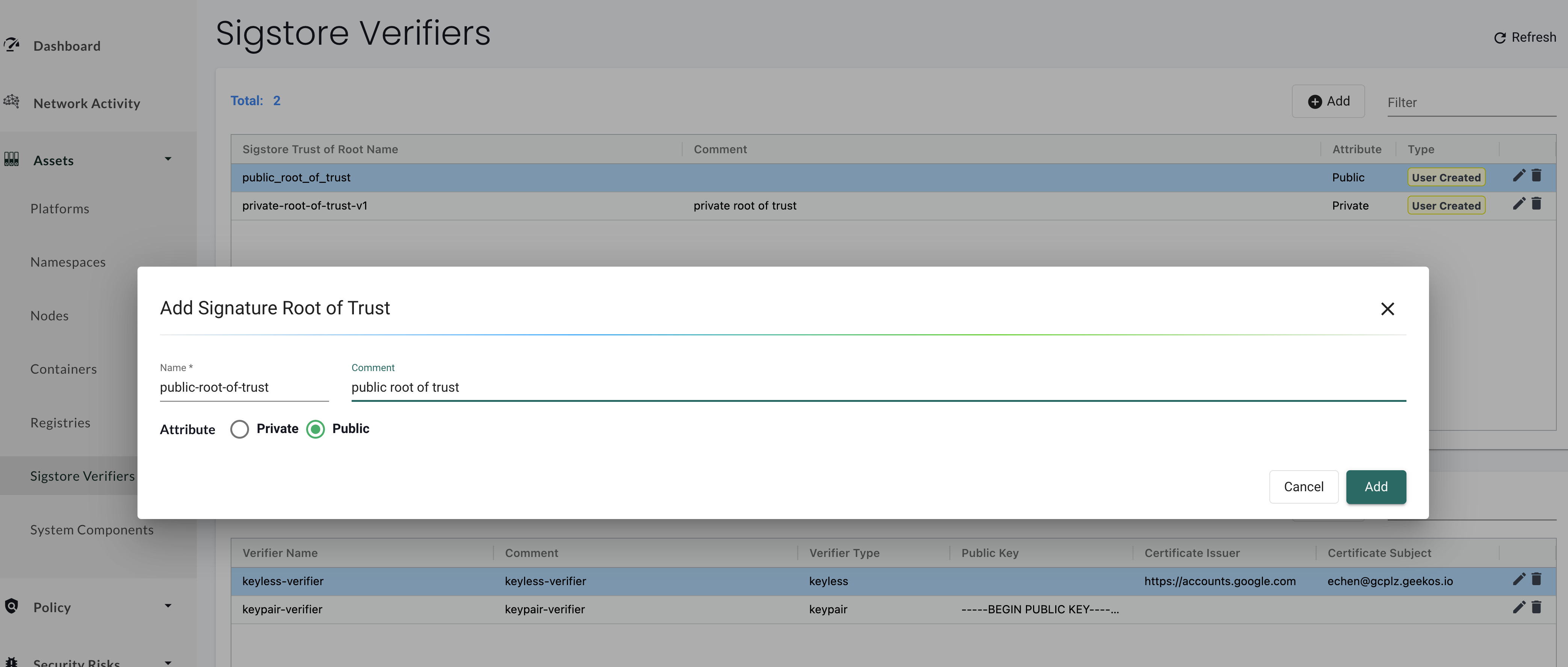
First, configure a root of trust. This can either be a public or private root of trust, depending on the Sigstore deployment used to generate signatures. If you have deployed your own instances of Sigstore's services, select the private root of trust option.
A public root of trust does not need any additional configuration outside of giving it an easily referenced name.
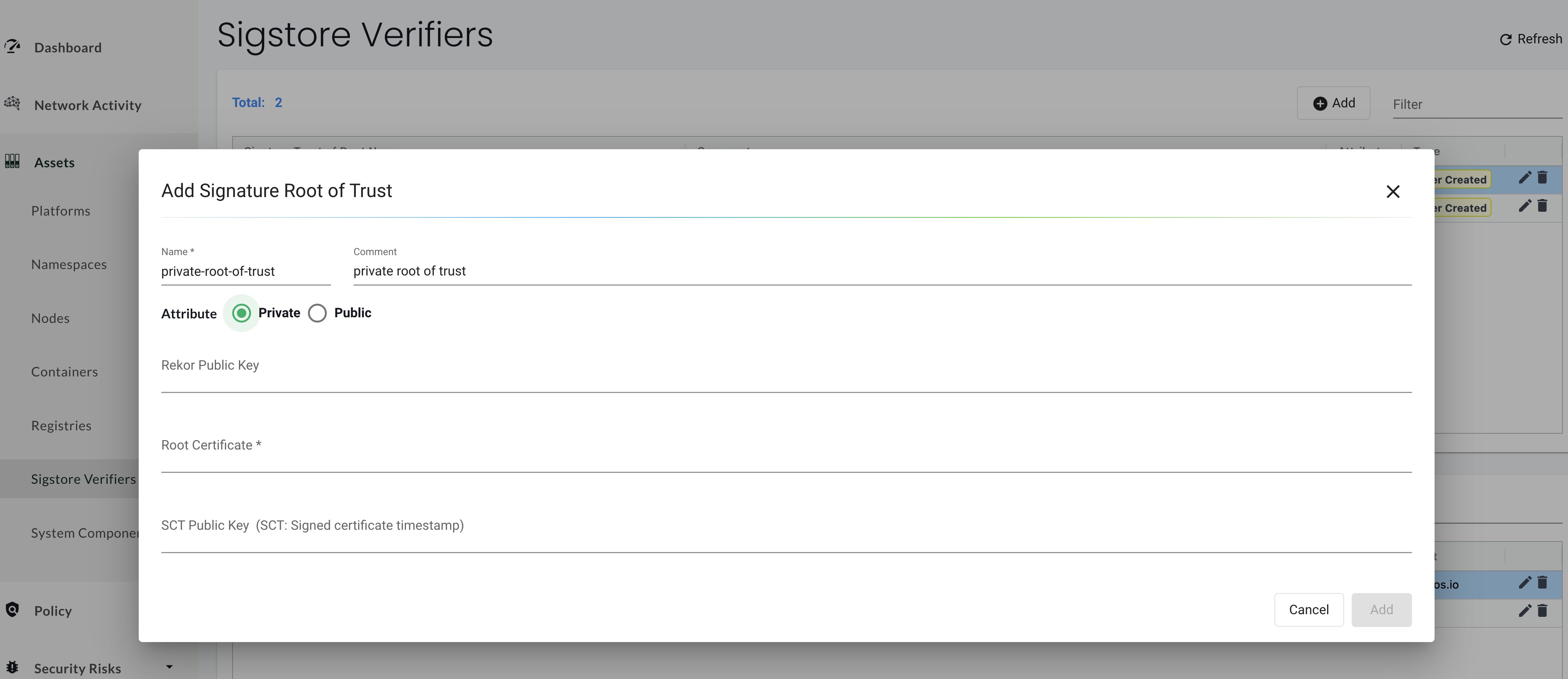
A private root of trust requires the the keys and/or certificates from your privately deployed instances of Sigstore's services.
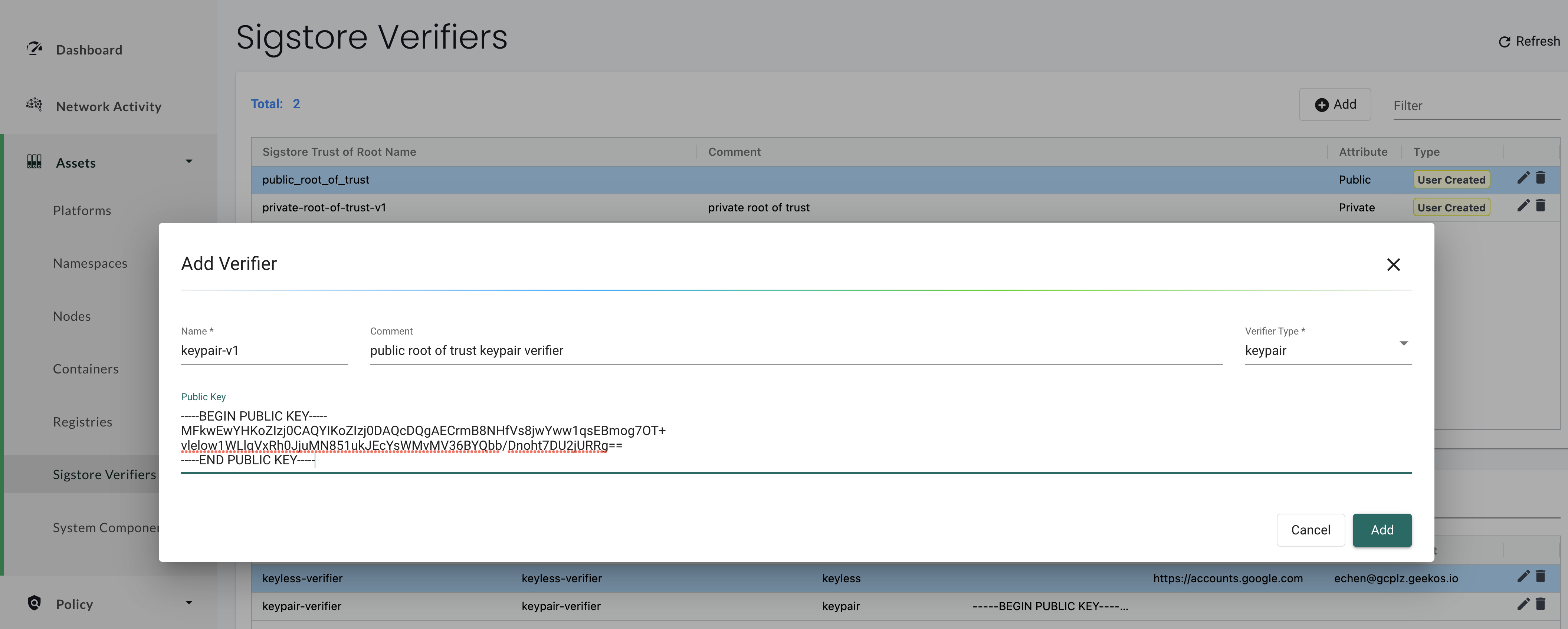
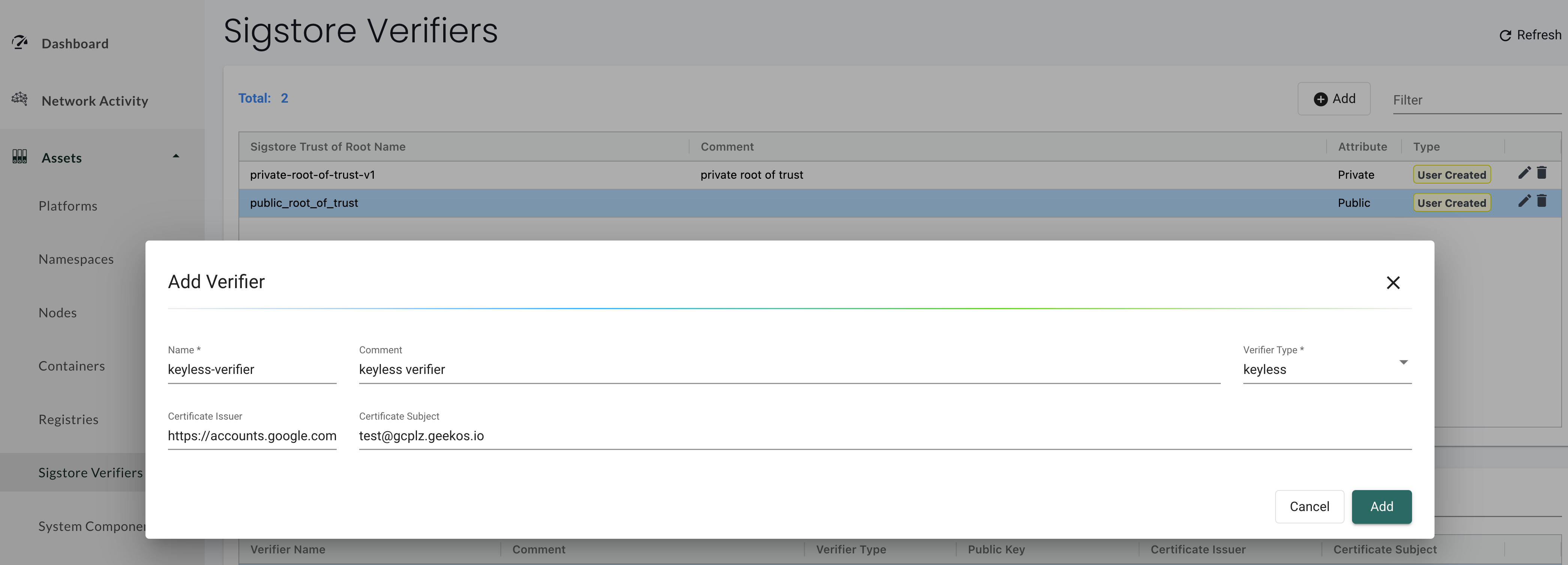
Next, for a given root of trust, configure each of the verifiers that you would like to use during admission control. There are two types of verifiers: keypair and keyless. A keypair verifier would be used when trying to verify an image signed by a user-defined private key. A keyless verifier would be used when verifying a signature generated by Sigstore's keyless pattern. More information about the Sigstore signing methods can be seen here.
To configure a keypair verifier, provide a name, and a public key corresponding to a target private key.
To configure a keyless verifier, provide the OIDC issuer and identity used during signing.
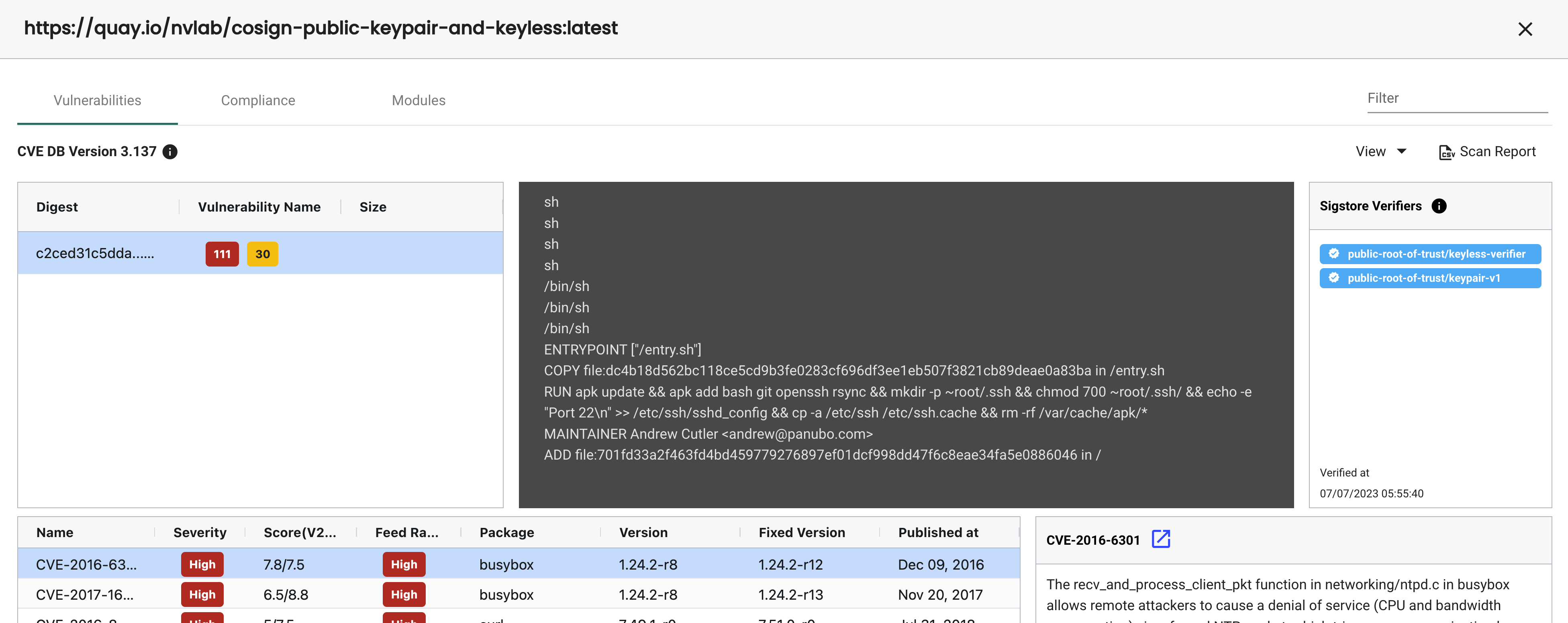
Note that after root-of-trust and verifier configuration, an image must be scanned in order to determine which verifiers the given image's signatures satisfy.
The configured verifiers that an image satisfies can be viewed in the upper right section of a given image's scan results in Assets->Registries. If an image is not signed by a verifier, it will not appear in its scan results.
To reference a particular root of trust and verifier in an admission control rule, join the two names with a forward slash like so: my-root-of-trust/my-verifier.
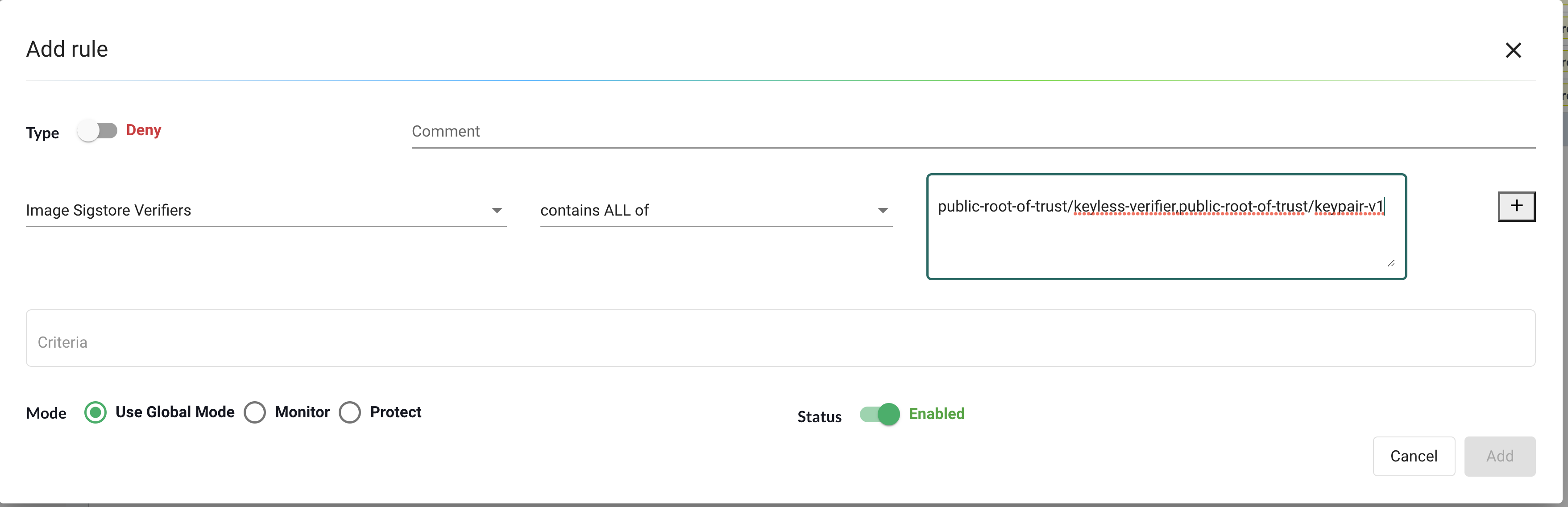
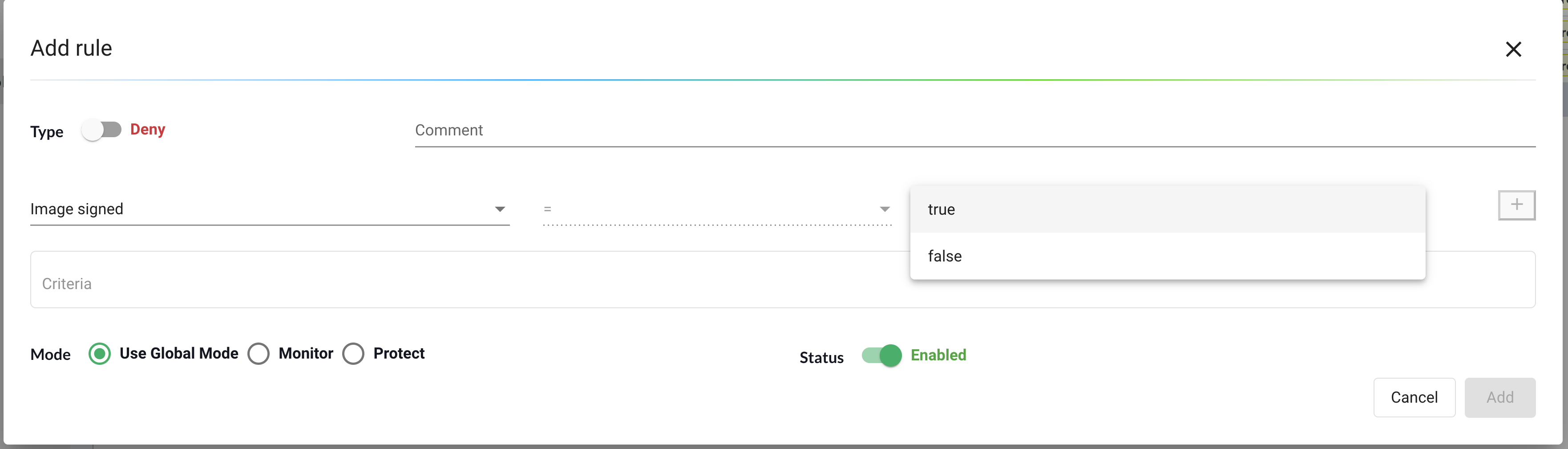
To require an image be signed in an admission control rule, set the True/False value for the Image Signed criteria.